Few things strike fear in the hearts of IT professionals as quickly as breaches in data security. Reporting requirements force public disclosure for some of these breaches, but far more go unreported, making it difficult to assess the true scope and cost of failed security.
We recently opened a Twitter chat (#datachat) with SQL Server and security experts to find out what more about data security and what they recommend doing to improve it. We were joined by: Brian Kelly (SQL Server MVP and Enterprise Systems Architect at AgFirst Farm Credit Bank), Tom Roush (Lead Database Administrator at Avanade), Steve Karam (Oracle ACE and Technical Manager at Delphix), , Denny Cherry (SQL Server MVP and founder of SQL Excursions), Karen Lopez (SQL Server MVP and Sr. Project Manager / Architect at Infoadvisors,), Joey D’ Antoni (Solutions Architect and Anexinet), Mark Holmes (Senior Database Administrator at West Notifications), Argenis Fernandez (Senior Database Monkey at Survey Monkey, Nancy Hidy Wilson (SQL Server Specialist at T-Services North America), and Thomas LaRock (SQL Server MCM and MVP, and Technical Evangelist at SolarWinds). (We even had a guest appearance from information security expert and professor at Purdue University, Eugene Spafford!)
Ensure you encrypt, at rest and in motion
Most experts agree that one of the easiest ways to secure data is encryption, as Tom LaRock notes here:
With encryption, data is translated into a secret code, and you use a key or password to decode or decrypt that file to read it. To make matters more complex, data encryption must extend to wherever that data lives and however it is transferred.
Consider the example offered by Tom Roush, in which even data at rest can be compromised by an application developer who accesses it for a cool new app without understanding the sensitivity of the data or how to preserve its security:
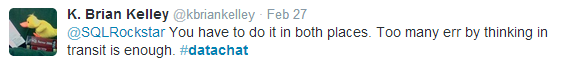
Brian Kelly notes that it’s easy—and dangerous—to overlook the obvious, such as not encrypting backups on site:
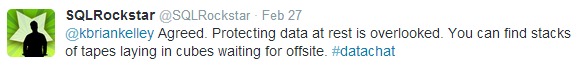
Even leaving tapes unsecured in a physical location can compromise otherwise solid security measures:
To be effective then, as Brian Kelly notes, encryption must account for data when it is in motion and when it is at rest:
Apply the principle of least privilege
The principle of least privilege means giving each user only as much access to data as is required for him or her to do a job. Sometimes referred to as the principle of minimal privilege, least authority or least-privileged user account (LUA), this approach helps protect information systems from malicious or unintended behaviors, and from faults in the system.
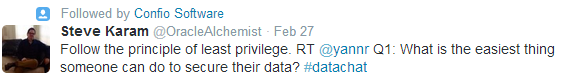
For many, this approach is foundational to a well-designed and executed security strategy, and ranks as one of the best or easiest things to do to secure data, as Steve Karam notes here:
Brian Kelly notes that, to be effective, the least privilege approach must be applied consistently, regardless of the environment or system that is in place.
See security as an enabler, not a disabler
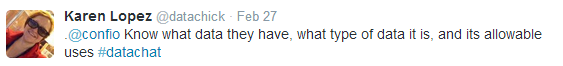
Specific tactics not withstanding, our experts agreed that securing data requires a comprehensive and consistent approach. As Karen Lopez stated, this approach starts with developing a deep understanding of what data and what types of data an organization has, and how that data should be used:
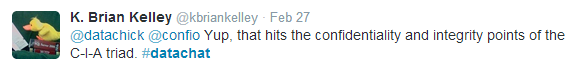
This forms, as Brian Kelley notes, two of the three pillars referred to as the C-I-A triad (for confidentiality, integrity and availability):
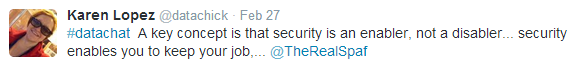
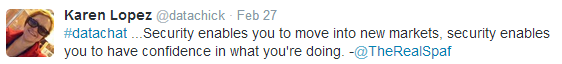
And the foundation under this triad, as Karen Lopez pointed out by referencing the work of Eugene Spafford, one of the world’s foremost experts on information security, is an understanding of security as an enabler–security as what allows you to have confidence in what you’re doing:
When an organization embraces security as an enabler, shifting away from viewing security as a time and budget killer, it becomes possible to align the right resources behind a robust and proactive security strategy that promotes growth.
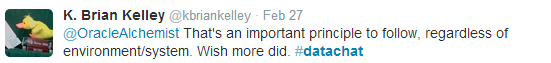
Leave a Reply