Large and very public data security breaches, such as were announced by Target and Nieman-Marcus at the end of 2013, seem increasingly common in frequency and astonishing in scope. Although the actual number of incidents in 2013 was down from 2012, according to Dataloss DB (http://datalossdb.org/ ), security remains a top priority for data professionals everywhere.
To find out what the biggest challenges are for businesses in addressing data security, we invited SQL Server and security experts to share their insights via a Twitter datachat (#datachat). Our #datachat panelists included: Brian Kelly (SQL Server MVP and Enterprise Systems Architect at AgFirst Farm Credit Bank), Denny Cherry (SQL Server MVP and founder of SQL Excursions), Karen Lopez (SQL Server MVP and Sr. Project Manager / Architect at Infoadvisors), Darcy Lussier (SQL Server MVP and Solution Architect at Online Business Systems), Mark Holmes (Senior Database Administrator at West Notifications), Argenis Fernandez (Senior Database Monkey at Survey Monkey, Nancy Hidy Wilson (SQL Server Specialist at T-Services North America), and Thomas LaRock (SQL Server MCM and MVP, and Technical Evangelist at SolarWinds). (Plus, a special guest appearance from Eugene Spafford, leading authority on information security).
Challenge 1: Increase awareness and education of security best practices
By far the most common challenge in data security, according to our panel, is a need to increase awareness and education, both within IT and in the general business community. On the IT side, Brian Kelley shared a statement from Jay Bavisi, a leading security expert and president of EC-Council, who posits that 99% of future IT workers don’t understand secure coding practices. (Interestingly, Kelley also noted that the EC-Council’s own web site was susbsequently hacked):
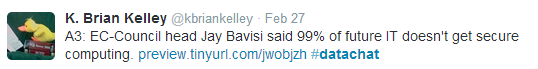
This pervasive lack of awareness about security—why it is critical and how it enables business, as Eugene Spafford asserts—keeps business leaders from making it a priority, as Tom LaRock notes here:
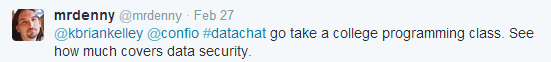
One reason for this state of affairs is that security isn’t included in IT-related curricula. For example, Denny Cherry asserts that most IT professionals don’t have experience with security because best practices aren’t taught, and security is rarely covered in college-level programming classes:
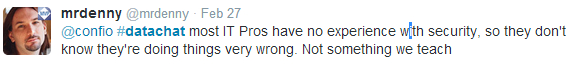
Outside of IT, the lack of awareness manifests itself in business users when they bypass security measures, for example, by transporting sensitive data via non-secure physical measures, such as USB drives, or sending sensitive data via e-mail, as Darcy Lussier points out:
Challenge 2: Make security everyone’s business
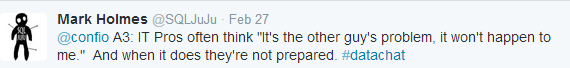
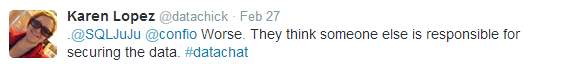
One result of the lack of education and awareness is that everyone thinks security is someone else’s issue, as Mark Holmes tweeted and Karen Lopez echoed:
The someone-else’s-problem approach is easy to see in action; Tom LaRock shared the example of developers coding applications using system administrator access without understanding the data being accessed or the risks in exposing it:
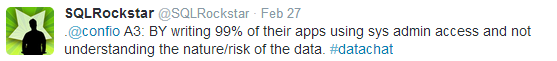
Argenis Fernandez offered the example of end users who keep the often- insecure default access information provided for applications, even when they’re encouraged to change the defaults:
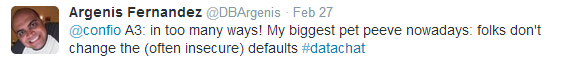
Sometimes, this attitude shows up as a belief that if it’s inside the firewall, it isn’t a security issue, but as Brian Kelley points out, what’s inside the firewall is perhaps the biggest threat:
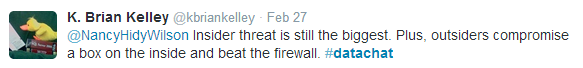
And, as @phra95w17ch points out, social engineering, not technology, plays a significant role in exploiting that inside-the-firewall threat:
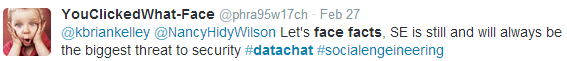
In reality, Tom LaRock says, data security is the job of every single person—employee, vendor, contractor, partner, customer—who has access to the data.
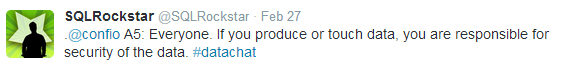
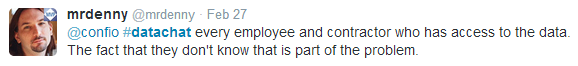
When any person in the chain of people who touches data doesn’t have this understanding, they contribute to the overall security challenge, according to Denny Cherry:
Challenge 3: Allocate adequate resources to data security
When businesses understand the importance of security, it’s easier to overcome the challenge of acquiring resources to support security implementations, another challenge cited by our panelists, including Nancy Hidy Wilson in this tweet:

Denny Cherry notes that this can sometimes even lead to security being cut altogether when a project’s budget or timeline is threatened:
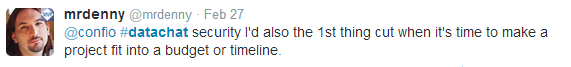
And Brian Kelley agrees that security implementations can run up against the demands of projects costs and schedules:
Challenge 4: Lobby to simplify regulations and streamline data security compliance and reporting
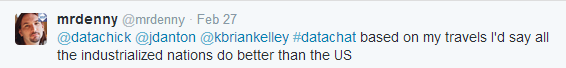
Finally, our panelists noted that geography and politics play a role in making security challenging. In Denny Cherry’s opinion, the U.S. has much to learn about data security, including data privacy, from other countries:
What has evolved in the U.S. is a complex set of federal and state laws and policies related to data security, creating a kind of patchwork of regulations that’s difficult to navigate, Karen Lopez tweets:
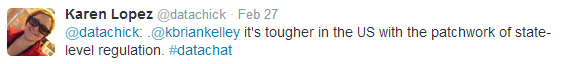
Brian Kelley agrees, stating that this state-by-state approach complicates an already complicated set of issues:

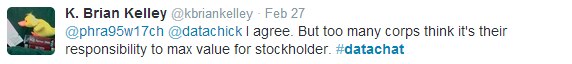
It’s important, too, not to lose sight of the fact that data security is a corporate responsibility that transcends regulatory requirements, as @phra95w17ch points out:
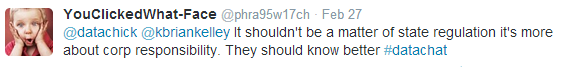
According to Brian Kelley, data security and security regulations mandate a corporate balancing act, sometimes pitting shareholder value against the very real need for resources to support security initiatives:
Embrace data security to transcend the challenges
In the end, despite the many issues that challenge businesses and governments in implementing adequate data security—from lack of education to lack of ownership to lack of resources to a daunting array of regulations—organizations must embrace security as an enabler. Eugene Spafford, one of the world’s foremost experts on information security, has long advocated that organizations must consider security, not as a burden, but as an enabler—something that allows you to have confidence in what you’re doing.


Leave a Reply