Although data security breaches seem to have become more commonplace, it’s challenging to assess the true scope of failed data security. Regulations for protecting data and reporting breaches vary widely with geography, so it’s reasonable to assume that what we hear about in the media represents only a percentage of the full problem.
To learn more about Oracle data security, including best practices for data security, we held a Twitter datachat (#datachat) with Oracle and security experts. We were joined by: Pete Finnigan (world-recognized expert in Oracle security and founder of PeteFinnigan.com), Rusty Schmidt (Senior Systems Analyst at Apollo Group), Steve Karam (Oracle ACE and Certified Master, and Technical Manager at Delphix), Kellyn Pot’Vin (Oracle ACE Director, Oak Table Member and Consulting Member Technical Staff at Oracle), and Dean Richards (Manager of Sales Engineering, SolarWinds).
1. Know where your data is
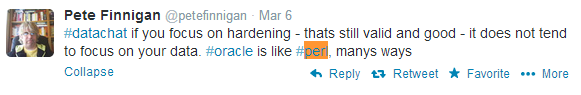
According to Pete Finnigan, implementing data security requires a clear understanding of the difference between securing data and securing databases, and that this starts with understanding where the data is, and who and how the data is being used:

Hardening has its place, and must absolutely be done but, says Finnigan, the data often gets overlooked:
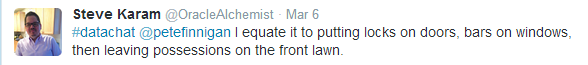
Failure to secure the database but not the data is something like putting locks on the front door of your house, and ignoring the fact that you’ve left possessions on the lawn, as Steve Karam tweets:
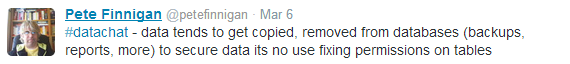
Those “things left on the lawn” include all the different ways data can be copied and accessed, including methods of access than can’t be controlled via the permsisions table, as Finnigan notes:
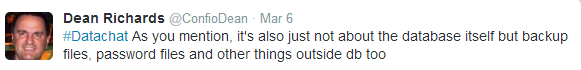
Dean Richards goes on to underscore this critical point, noting that things outside the database, such as password files, can put data security at risk:
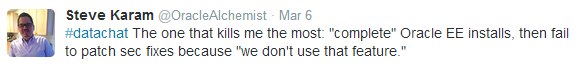
Sometimes, risk to data security is introduced by not maintaining a holistic view of the threats, including not keeping software up to date, as Karam points out is often the case when implementations include a full install of Oracle Enterprise Edition, but security patches aren’t applied because a specific feature isn’t in use:
In fact, Finnigan notes that the scope of data security must extend to all the ways created to access that data, some of which the DBA may have no control for:

2. Next, consider access
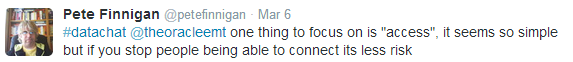
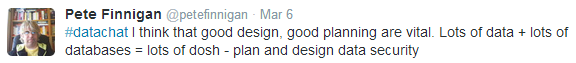
Once you have a clear understanding of where the data is, the next focus is access. Restricting access is, as Finnigan points out, still one of the most useful ways to secure data:
Richards shares that, in his experience, a least-privilege model has been very useful. Using this approach, each user is granted only as much access to data as is required for him or her to do a job. This approach helps protect systems from malicious or unintended behaviors, and from faults in the system.

Designing user access to meet the needs of the data is critical, Finnigan says:
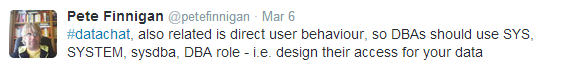
For example, it’s important for DBAs to use the SYS, SYSTEM, sysdba and DBA roles effectively, as Finnigan tweets here:
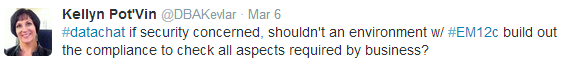
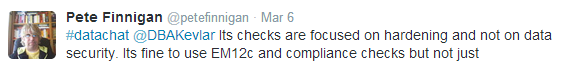
In this exchange with Kellyn Pot’Vin, Finnigan also points out that it’s not enough to use a tool like Oracle Enterprise Manager (EM12c) to build out the compliance to check all aspects required by the business, because these tools focus on hardening and not on data security:
When you get the profile designs, strong password and the privileges of direct connect users done right, you’ve laid the foundation for an excellent security model, according to Finnigan:

3. Make sure data security is a business priority
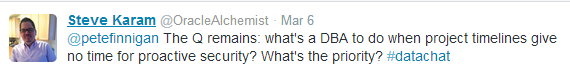
Data security is much more than an IT issue. Underlying any well-designed and well-executed data security problem is a deep connection to business priorities. Several experts on our panel noted that data security often falls prey to project timelines and budgets, as Karam notes here:
Finnigan says that data security must be set as a priority by management:

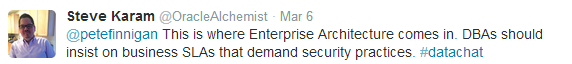
And, Karam tweets, DBAs should insist on business-based service-level agreements (SLAs) that mandate best practices for data security:
Ignoring data security is a gamble for any business to make, as Finnigan points out, with the least damaging outcome being data loss:
Data security breaches can result in far more than data loss, though, as Karam goes on to note, and can do more damage to a business than power loss, including downtime, business loss, reduced customer confidence and more:
Certainly there have been very public breaches of data security, most recently with Target at the end of 2013, but Finnegan recalls the LulzSec attacks on Sony in 2011, which were made possible by a lack of commitment to even basic data security at a corporate level (for a refresher, see this story in PC Magazine http://www.pcmag.com/article2/0,2817,2386397,00.asp):
Finally, as Richards summarizes, if the CEO and CIO don’t fund data security initiatives, bad things can happen:
Security should be a proactive process
Data security must encompass the data and the many ways in which data is used. Our experts all agreed that in order to design an adequate security approach, it’s critical to know where data is, how it’s used and by whom. Data security must be a strategic initiative with corporate backing that is focused on proactive security that enables organizations to conduct business successfully with minimized risks.
When an organization embraces security as an enabler, shifting away from viewing security as a time and budget killer, it becomes possible to align the right resources behind a robust and proactive security strategy that promotes growth.
Leave a Reply