Sometimes applications are built in the cloud with no need to connect to your on-premises IT. But far more often applications in the cloud need to talk to applications in your existing data centers. We usually want network routing over a connection between our cloud and our data centers. This connection between on-premises and cloud is even more important during a cloud migration. Part of your IT has moved but part is still on-premises. AWS offers several ways to connect your on-premises data centers to your VPCs. Direct Connect is a dedicated WAN link into an AWS location. A VPN connection uses the Internet but puts your traffic inside an encrypted tunnel. AWS has multiple VPN options too. You can have a hardware VPN appliance or software in the AWS location. Either way, you also need a VPN appliance in your datacenter too.
I am going to connect the VPC I created in a previous post. I am going to use an IPSec VPN from my firewall to the VPC.
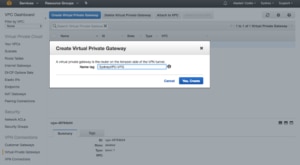
First I need a Virtual Private Gateway (VPG). This is the router for the AWS side of the VPN. In the VPC dashboard, select “Virtual Private Gateways” and click “Create Virtual Private Gateway”:
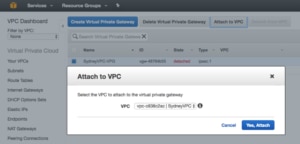
All that the VPG needs is a name. Since this VPG will be for my Sydney VPC I included the VPC in its name. Now I click the “Attach to VPC” button and select my SydneyVPC from the list. The process to attach takes a few minutes.
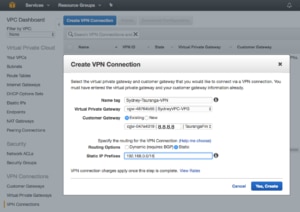
Now that I have a VPG for the AWS side of the VPN connection I can tell AWS about my firewall. This is the Customer Gateway. All it needs is a name and public IP address as well as a routing protocol. I have a very simple configuration with separate IP ranges for my network and the VPC, so I am using static routing. For more complex networks, you can use BGP for dynamic routing.
AWS now knows where to find both ends of my VPN, so it’s time to connect them together. In the “Create VPN Connection” wizard I need to give the connection a name and choose both the VPG and Customer Gateway. Since I said static routing I also need to tell AWS what network is on the other end of the VPN. Notice that there are VPN charges, also it will take a while for the VPN connection to provision.
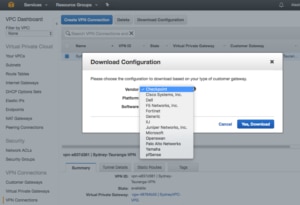
So far we have simply done the AWS side of the VPN, now we need to get the matching configuration onto our firewall. The simplest way to do this is to use the “Download Configuration” option to get a configuration file you can import into your firewall. There are a few options covering common firewall options. Once the configuration file is downloaded to your PC you can upload it into your firewall and establish the VPN connection.
In my case, the downloaded file was a text file with a description of the settings I needed to enter in my firewall’s VPN configuration. Once the details were in place the VPN connected. I could see its “UP” status on the “Tunnel Details” tab of the Sydney-Tauranga-VPN connection.
From my Internal network, I am now able to ping an EC2 instance in the Sydney-VPC. My on-premises network is now joined to my AWS VPC. Any applications I build in or migrate to the VPC will be able to access my on-premises servers.



Leave a Reply