More personal and proprietary data is available online than ever before—and many malicious actors want to get ahold of this valuable information. Using an intrusion detection system (IDS) is essential to the protection of your network and on-premises devices.
Intrusion detection systems are designed to identify suspicious and malicious activity through network traffic, and an intrusion detection system (IDS) enables you to discover whether your network is being attacked. There are many great IDS options available, but in my opinion SolarWinds® Security Event Manager (SEM) is a step above the rest. SEM enables real-time intrusion detection across your network and on-premises devices, and leverages many automatic capabilities designed to help optimize intrusion detection. A 30-day free trial of SEM is available.
What Is an Intrusion Detection System?
An intrusion detection system (IDS) is software specifically built to monitor network traffic and discover irregularities. Unwarranted or unexplained network changes could indicate malicious activity at any stage, whether it be the beginnings of an attack or a full-blown breach. There are two main kinds of intrusion detection system (IDS):
- A network intrusion detection system (NIDS) enacts intrusion detection across your entire network, using all packet metadata and contents to determine threats.
- A host-based intrusion detection system (HIDS) enacts intrusion detection through a particular endpoint, and monitors network traffic and system logs to and from a particular device.
The best intrusion detection systems are built to collect network traffic from all devices via NIDS and HIDS, thus increasing the chances of intrusion detection across your IT infrastructure.
How Does an Intrusion Detection System Work?
After data collection, an IDS is designed to observe network traffic and match traffic patterns to known attacks. Through this method, sometimes called pattern correlation, an intrusion prevention system could determine if unusual activity is a cyberattack. Once suspicious or malicious activity is discovered, an intrusion detection system will send an alarm to specified technicians or IT administrators. IDS alarms enable you to quickly begin troubleshooting and identify root sources of issues, or discover and stop harmful agents in their tracks.
Intrusion detection systems primarily use two key intrusion detection methods: signature-based intrusion detection and anomaly-based intrusion detection. Signature-based intrusion detection is designed to detect possible threats by comparing given network traffic and log data to existing attack patterns. These patterns are called sequences (hence the name) and could include byte sequences, known as malicious instruction sequences. Signature-based detection enables you to accurately detect and identify possible known attacks.
Anomaly-based intrusion detection is the opposite—it’s designed to pinpoint unknown attacks, such as new malware, and adapt to them on the fly using machine learning. Machine learning techniques enable an intrusion detection system (IDS) to create baselines of trustworthy activity—known as a trust model—then compare new behavior to verified trust models. False alarms can occur when using an anomaly-based IDS, since previously unknown yet legitimate network traffic could be falsely identified as malicious activity.
Hybrid intrusion detection systems use signature-based and anomaly-based intrusion detection to increase the scope of your intrusion prevention system. This enables you to identify as many threats as possible. A comprehensive intrusion detection system (IDS) can understand the evasion techniques cybercriminals use to trick an intrusion prevention system into thinking there isn’t an attack taking place. These techniques could include fragmentation, low-bandwidth attacks, pattern change evasion, address spoofing or proxying, and more.
Why Is Using an Intrusion Detection System Important?
An IDS enables you to enhance the security of your network devices and valuable network data by pinpointing suspicious network traffic and bringing it to your attention. Your network needs strong security to protect existing information and transfers of internal and external network data. Cyberattacks are increasing in sophistication and regularity, so it’s important to have a comprehensive and adaptable intrusion detection system.
Along with increasing network security, an intrusion detection system can help you organize critical network data. Your network generates tons of information every day through regular operations, and an intrusion detection system can help you differentiate the necessary activity from the less important information. By helping you determine which data you should pay attention to, an intrusion detection system can spare you from combing through thousands of system logs for critical information. This can save you time, reduce manual effort, and minimize human error when it comes to intrusion detection.
Gaining detailed, accurate visibility of network activity through an IDS can also help you demonstrate compliance. Intrusion prevention systems are built to detect, organize, and alert on inbound and outbound network traffic in depth, pinpointing the most critical information. By filtering through network traffic, an intrusion detection system could give you a leg up when it comes to determining the compliance of your network and its devices.
An IDS is made to optimize intrusion detection and prevention by filtering through traffic flow. This can save you time, energy, and resources while spotting suspicious activity before it turns into a full-blown threat. An IDS also provides increased visibility into network traffic, which can help you fend off and catch malicious activity, determine compliance status, and improve overall network performance. The more your IDS catches and understands malicious activity on your network, the more it can adapt to increasingly sophisticated attacks.
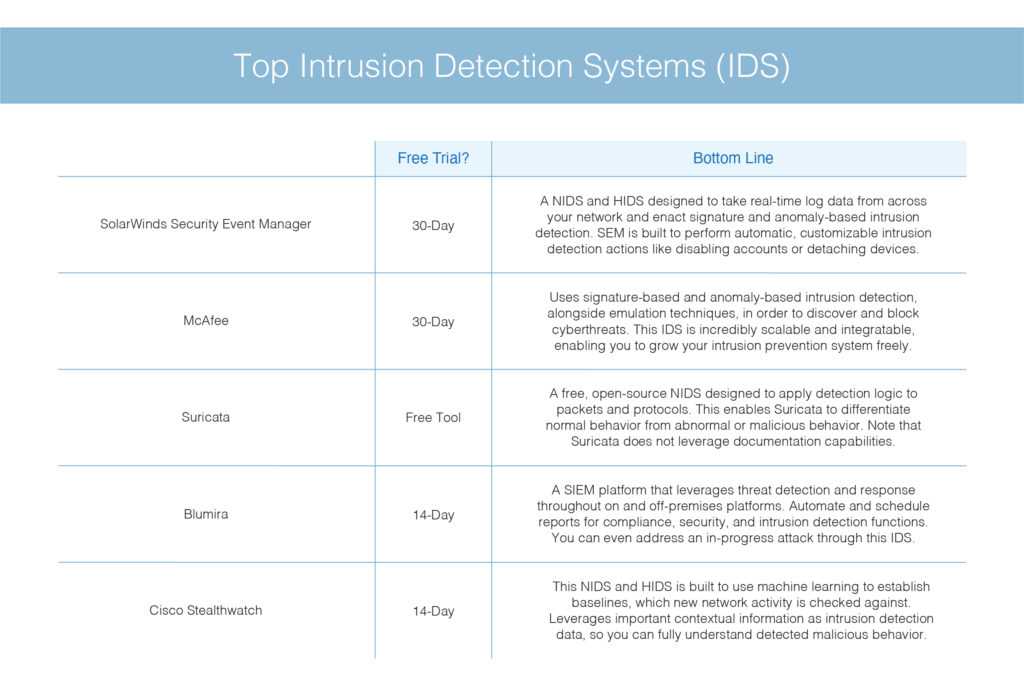
Recommended Intrusion Detection System (IDS) Tools
1. SolarWinds Security Event Manager
SolarWinds Security Event Manager (SEM) is designed to integrate real-time log data from across your infrastructure, enabling SEM to act as both a NIDS and a HIDS platform. This solution can let you discover all kinds of malicious attacks and help protect your network from harm. SEM is also designed to enact both signature-based and anomaly-based intrusion detection by comparing sequences of network traffic against a set of customizable rules.
Use SEM rule templates for immediate intrusion detection or create your own rules from scratch using an intuitive rule builder. SEM is also designed to organize active pattern correlations and sequence comparisons, listing them alphabetically or with associated categories. Filter through rules, view historical rule activity, and search for specific keywords with SEM.
SEM also enables you to develop in-depth assessment reports using out-of-the-box reporting templates or customizable templates built into the SEM interface. These reports make it easy to complete standard reporting to demonstrate compliance, complete security audits, and more. Along with reports, SEM can provide active response capabilities that automatically detect and respond to suspicious network traffic. These actions include logging off users, disabling user accounts, shutting down processes, and blocking IP addresses or detaching devices like USBs.
SolarWinds SEM is a powerful intrusion detection system (IDS) designed to fit your organization’s needs. With in-depth intrusion detection capabilities and other maintenance features, SEM enables you to perform high-quality intrusion detection on Windows, Unix/Linux, and macOS devices. Download a 30-day free trial of SEM.
2. McAfee
McAfee is an intrusion detection system (IDS) designed to bring real-time threat awareness to your physical and virtual networks. McAfee uses signature-based intrusion prevention and anomaly-based intrusion detection along with emulation techniques to spot and identify malicious activity. McAfee is also built to correlate threat activity with application usage, which can further prevent network issues stemming from cyberattacks.
The McAfee intrusion detection system is designed to collect traffic flow from switches and routers and uses SSL decryption to inspect inbound and outbound network traffic. This enables McAfee to comprehensively discover and block threats in cloud environments and on-premises platforms. To manage this in-depth visibility, the McAfee IDS leverages centralized management that could run actions like isolating hosts, limiting connections, enacting multiple attack correlation, and more.
A core benefit to McAfee is its scalability and integrability, which enables you to grow your virtual workloads or join forces with other McAfee platforms for more advanced threat defense and antivirus prevention. There’s a 30-day free trial of McAfee available for download.
3. Suricata
Suricata is a free, open-source network intrusion detection system (NIDS) that runs on a code-based platform. Suricata is designed to use signature-based intrusion detection to determine known threats and detect other suspicious behavior in real time. This enables you to quickly counterattack malicious activity found within your network.
Suricata is built to inspect multi-gigabit traffic and automatically detect protocols. By applying detection logic to each packet and protocol as it comes through, Suricata can determine normal behavior versus irregular traffic to detect malformed code. Suricata also uses protocol keywords, rule profiling, file and pattern matching, and machine learning to identify cyberattacks.
Although Suricata is a great open-source intrusion detection system (IDS), it’s missing critical documentation capabilities. This lack of documentation can complicate troubleshooting and makes it hard to reference the past and prepare for the future. However, if you’re looking for a simple yet steady real-time IDS, Suricata could be a good option.
4. Blumira
Blumira is a security information and event management (SIEM) platform built to enact threat detection and responses across your cloud and on-premises environments. Blumira is designed to continuously monitor your IT infrastructure for suspicious activity and misconfigurations, both of which could result in data leaks and compliance breaches. Blumira enables you to respond to an attack in progress and stop malicious actors in their tracks.
Blumira is designed to provide you with all relevant matched data, which can simplify your investigation into suspicious activity. With Blumira, you can analyze all network events, then sort through them for priority alerts. This enables you to focus on the most pressing threats at hand. Blumira also lets you assign responders to certain events for better intrusion detection management.
With Blumira, you can build your own intrusion detection reports and automate their options. This means you can schedule reports and run them periodically or save reports for safekeeping. Blumira reports enable you to dig deeper into intrusion detection system data. All this is available on a simple, easy-to-use interface. Download a 14-day free trial of Blumira.
5. Cisco Stealthwatch
Cisco Stealthwatch is an enterprise NIDS and HIDS for Windows, Linux, or macOS devices. Cisco Stealthwatch is an agentless intrusion detection system, which also enables it to scale to your growing business requirements. By leveraging a scalable IDS, Cisco Stealthwatch can help you prepare for whatever intrusion prevention methods are on the rise.
Cisco Stealthwatch enacts intrusion detection and response through entity monitoring, which uses machine learning to establish baselines of acceptable behavior. Cisco Stealthwatch also uses a behavioral modeling approach forvisibility into your network’s endpoints, cloud-hosted services, and data centers. Anomalies or suspicious activity found throughout these monitoring methods is correlated to service alerts, which can help you quickly address intrusions.
Cisco Stealthwatch is designed to detect malware in encrypted network traffic without having to decrypt. This helps with policy compliance where private data is concerned. Along with security benefits, Cisco Stealthware is built to contextualize intrusion detection data by including information like user, time, place, and application used. This brings you a comprehensive knowledge of threat activity, enabling you to properly examine the right data. Download a 14-day free trial of Cisco Stealthwatch.
Final Thoughts on Intrusion Detection Systems
An intrusion detection system is a critical component to protecting your on-premises and cloud-hosted IT environments from malicious attacks and cyberthreats. There are many intrusion detection systems available today—the IDS options in the list above are just a few of the platforms dedicated to intrusion detection and prevention.
In my opinion, SolarWinds Security Event Manager (SEM) is a top intrusion detection system, designed to leverage both NIDS and HIDS using signature-based and anomaly-based intrusion detection methods. SEM is a comprehensive and powerful IDS with support for real-time alerts, rule filtering, automatic actions, and in-depth insights into intrusion detection. Download a 30-day free trial of SEM today.