Oracle designed Cloud Control to integrate into and manage the most security-hardened data centers. Security functionality is built into the product, both at the application and underlying component levels. The Cloud Control application extends built-in features to tighten its own security. These features are available both through the Console and in executables (such as
emctl under the OMS and Agent homes). The underlying components, the Oracle Database 11g and Oracle Application Server 11g instances (Oracle HTTP Server in particular), also provide their own built-in security services that Cloud Control co-opts to protect itself.Consider Table 1 our “big board” on Cloud Control security. It lists the primary Cloud Control security goals and how you achieve them.
Let’s run through the big board and break it down this way:
- Cloud Control Security This covers a particular aspect of Cloud Control security: how to secure data transmitted between CC components. Security systems should implement secure connections between all critical and sensitive points of communication. For Cloud Control, the communication points are between its components: Repository, OMS, Agents, and Console, and such communication is secured by strong encryption.
- SSO and EUS If you use either of these products, evaluate using them in tandem with GC for authentication.
- Firewalls Configuring CC with firewalls is an important security matter, but a relatively straightforward process. Before installing CC, open the firewalls between CC hosts to all traffic on CC communication ports.
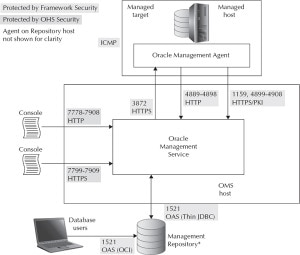
Let’s focus in now on securing data transfer between GC components. The major contributor to preserving the privacy and integrity of GC traffic is EM Framework Security (“Framework Security”), so named because it protects the flow of data within the CC framework (that is, between Agents, OMS, and Repository). Bringing up the rear is the Oracle HTTP Server bundled with CC, responsible for protecting browser/Console exchanges and restricting Console access based on client network characteristics. Let me introduce this dynamic duo by drawing the big picture, which you can refer back to as we delve in. Figure 1 shows how Framework Security and Oracle HTTP Server (OHS) together protect all GC communications.
As you can see, Framework Security and OHS are tightly integrated and complement one another to secure all data channels between GC components. Table 2 presents this same information in tabular form for those of you who find tables more palatable than figures.
Both Figure 1 and Table 2 detail the security method employed to protect data flow, whether the method is considered part of Framework Security or OHS security, and the ports where communications take place. HTTPS signifies that Secure Sockets Layer (SSL) is used, which is an industry-standard technology for encrypting data.


Leave a Reply